The ransomware paper (part 1): What is ransomware?
I spend about half my conversational time these days answering questions about ransomware, including how to prepare for it, prevent it and recover from it.
Around May 2021, right after the Colonial Pipeline ransomware attack, I decided to record these conversations, writings and responses in detail and turn them into an output that may benefit others. Basically, I turned it into a mini-research project.
The things I learned and planned to address in this ransomware series are:
- A lot of the population, including some cybersecurity professionals, don’t actually know what ransomware is.
- Some confusion around ransomware stems from some vendors attempting to capitalize on ransomware’s fear and media coverage.
- We all (industry professionals) must do a better job of disseminating information about new or recurring threats — in a digestible manner and for more than just our community.
The first entry in this ransomware series will focus on the first item: what exactly is ransomware?
What does ransomware do?
Let’s talk about what ransomware is and isn’t.
Ransomware is a piece of multi-functional malicious software created specifically to encrypt, obfuscate or “scramble” your data so that you can longer read or interact with it properly. In addition, it can usually spread itself across an environment and repeat this encryption process as it encounters other systems and data.
This second function is why we can’t say ransomware is just encryption. Encryption is one part of the operation, but spreading and moving around inside an environment is separate.

Download Keatron's free paper, "The ransomware paper: Real-life insights and predictions from the trenches."
How ransomware infects a system
Great, we’ve identified what ransomware is. But how does ransomware get into our environment and infect a system? That is usually through an exploited vulnerability, whether it be machine, code or human.
One of the most common misconceptions I've heard is that people think ransomware describes software that includes the ability to break into your computer or network using new and mystical techniques. The truth is much simpler: 100% of the ransomware attacks in the news primarily resulted from exploiting low-hanging vulnerabilities to gain entry.
Ransomware happens as a result of someone getting into your environment without authorization or permission. If a friend of yours said she woke up and a person she didn’t know was changing her passwords and door locks — and she could no longer log in to her Netflix, Amazon or Hulu accounts — wouldn’t your first question be, “How did this person get into your house?”
When a company is a victim of a successful ransomware attack, it is the equivalent of someone you have never met figuring out how to get into your house. They then change all your passwords, lock all your TVs and change your door locks — without you knowing it was going on until they asked you for money to unlock it all or change it back.
When you hear that a company was a victim of ransomware, your immediate reaction should be, “How did the ransomware operators get inside to deploy the ransomware?”
Ransomware and MITRE ATT&CK
In the world of cybersecurity, we often reference a framework known as MITRE ATT&CK® to describe real threats based on real-world observations.
ATT&CK is loosely laid out in the order most techniques are used or deployed. The encryption of your data via ransomware happens no earlier than step 4 (“Execution”) or, more likely, step 12 (“Command and Control”).
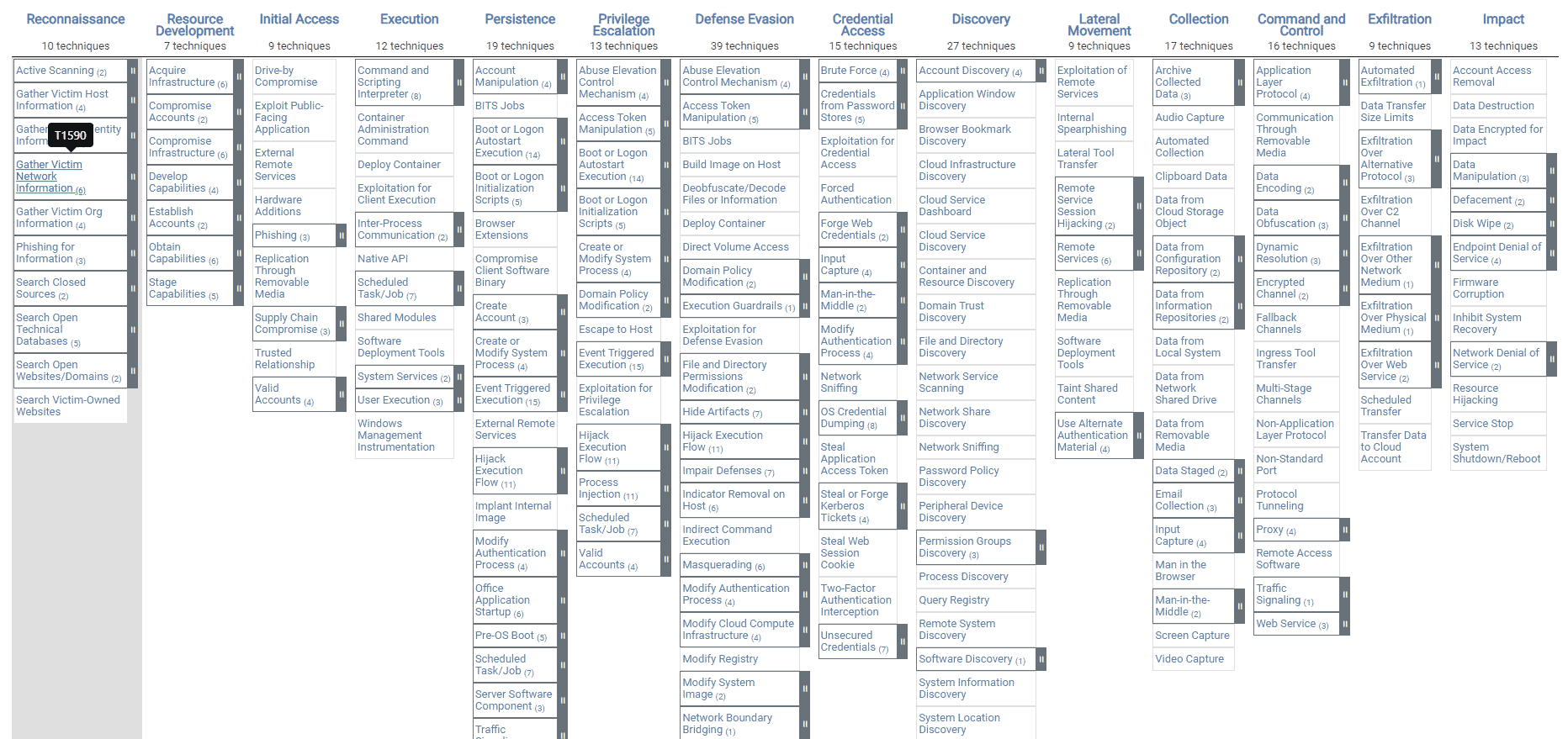
Source: MITRE Corporation
Nowadays, ransomware actors tend to do a lot of internal recon on your organization once they’re inside since the objectives may change — a lot of the ransom requests have become multi-headed. That means by the time you get the “send us bitcoin to get your data back” message, you’re in step 1 of your response, but they’re in step 12 of their operation.
Take a moment to appreciate how behind the curve you are at that point.
How ransomware encryption works
What exactly does it mean when we say someone “encrypts” your data? To answer that, we will do an exercise to give you a fundamental understanding of what encryption is and how ransomware encryption works.
Let’s pretend your entire collection of data only consisted of the word “cat.” Our word/data is “cat,” and we’re going to encrypt it using a secret encryption key of 601. So it would look like this:
Data c a t
Key 6 0 1
Encrypted data i a u
See what we did there? We incremented or rotated each letter of the original word by the number of characters of the associated key aligned with that letter.
Take “c,” for example. If we add 6, we have d > e > f > g > h > i. So “i” is six spaces from “c,” which is how “c” became “i.” Let’s move on to the “a.” The “a” has a key value of 0, which means we don’t shift it at all, and it stays “a.” Now finally, the “t.” The “t” has a key value of 1, so we shift it over by one letter, which makes it “u.” That’s how “cat” ended up being “iau.”
We are describing a simple Caesar Cipher, which is just one of the many types of encryption ciphers, and there are much more complex algorithms or instructions than just rotating the letter by a certain amount. These much more complex algorithms and keys are what most ransomware operators use.
Can you imagine if I had said rotate the “c” by 45,677 characters? The alphabet would start over at “a” after 26, and we would repeat this for a while. It would have taken a while to do that by hand, but if we’re good at math, we can cut down on the work of figuring it out using scary things like algebra, calculus and other advanced math.
So when someone encrypts your data with ransomware, they are doing a more advanced version of this, and they are keeping the key secret so that you have no chance of figuring out how much your data was “rotated.”
Now, this little lesson won’t make you ready to tackle a ransomware operator head-on, but it should give even a novice an idea of what it means when a ransomware attacker “encrypted” your files. It makes all your data useless in a matter of seconds.
Phishing simulations & training
Ransomware starts with gaining control of systems
I want to remind everyone that ransomware happens after an actor has already gotten control of your system — and the bigger problem is usually that loss of control.
One of the most successful ransomware campaigns ever was the 2017 WannaCry campaign. One of the primary ways WannaCry spread was through a previously unknown vulnerability, aka zero-day vulnerability, that led to the creation of a zero-day exploit named EternalBlue. This exploit was primarily how the WannaCry ransomware was distributed and wreaked havoc across the world.
Now that we’ve covered the basics of what ransomware is, the next segment in this series will examine overlooked or wrong things in the news concerning ransomware.